Theoretically, quantum computing poses a huge threat to the security of blockchain and cryptocurrencies. Just how real is the threat and what should we do to avert it?
Before we start, there are two things you need to keep in mind:
- The internet runs on cryptography. Anything that needs digital identity encryption — be it digital services like your email and social account or more critical use-cases like bank passwords and web server access.
- Web 3.0 will change the (and your) world. When it comes to digital identity or financial services, blockchain-based tech, with cryptocurrencies being an integral part, will have a significant impact on digital services. We’re moving from ‘transfer of information’ to ‘transfer of value’, and Web 3.0 is the infrastructure that is being built on. (quote inspired by Nitin Gaur, Director @ IBM, and his session at Masters’ Union)
But now, there’s a new kid on the block — quantum computing. With its ability to ‘brute force’ even the most stringent commonly used encryption standards, quantum computing will break today’s cryptography, leaving digital identities, blockchain-based technologies and digital currencies vulnerable to attack.
Is this a valid concern?
TL;DR — It’s a decade from happening, but there are things we can do to prevent it — if we start preparing now.
What’s the threat, exactly?
Here’s a quick refresher. Blockchain is essentially a database chain composed of many blocks (the infamous ledger). Blocks contain:
- Time-stamped transaction records
- Information about the participants of a transaction in the form of a digital signature
- Information that distinguishes the block from others in the form of a cryptographic code or “hash”
This information is publicly available and distributed across a huge network of computers.
It is also immutable. Each block contains the cryptographic hash of the previous block, and each node checks any change that is made to any block in the chain — making it virtually impossible for bad actors to manipulate any records. Because of this, blockchain offers more transparency and security than many centralized players.
Now, the problem is that blockchain uses public-key cryptography to authenticate transactions. Specialized computers are given the task of solving a cryptographic algorithm in order to create digital signatures and validate transactions.
These use one-way mathematical functions to create validation functions — a public key that’s exposed and a private key that’s only available to the user. This works, because to derive a private key from a public key would take a very long time for today’s computers — millions and billions of years to be exact.
But quantum computers aren’t like today’s computers.
They rely on the principles of quantum mechanics. Instead of bits, they use quantum bits, which are held in superposition and able to be in more than one state at a time. This allows them to perform certain tasks exponentially faster than classical computers.
Plus, qubits in the same system are entangled, meaning that changes in the state of one result in changes in the state of the others. This makes it possible for qubits to be part of several calculations at once.
(We’ve also taken a closer look at the real business value of quantum computing here)
This means that a quantum computer could solve today’s cryptographic algorithms in days rather than millennia.
When blockchain goes kaboom!
With a coherent enough quantum computer, criminals could derive users’ private keys from their public keys and use them to:
- Hack account passwords, forge signatures, and impersonate the owners of cryptocurrency, NFTs and other digital assets
- Manipulate transaction history and double-spend coins
- Reuse addresses to steal currency
Is this likely to happen anytime soon?
Opinions vary, but most experts agree that we can expect this to happen in about a decade.
Today’s quantum computers definitely couldn’t achieve any of this — it’s hard to maintain qubits in their working state, and quantum computers are prone to error due to processes like decoherence.
Thankfully, today’s quantum computers just don’t have the thousands of qubits that would be needed to perform such calculations.

But quantum computing is rapidly advancing.
In November 2021, IBM released its Eagle quantum computing chip which, at 127 qubits, is the first to cross three digits, surpassing Google’s 72-qubit quantum computer.
IBM plans to release one with 1,121 qubits, called Condor, by 2023.
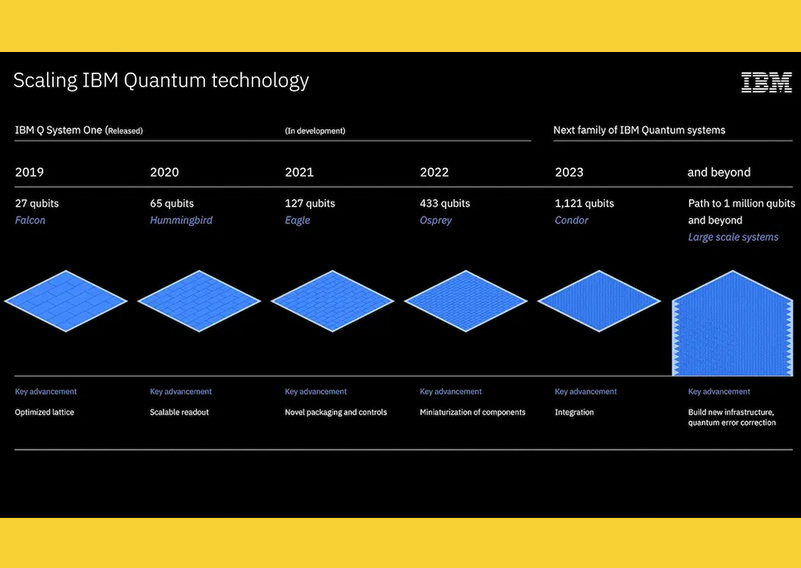
If quantum computing continues to advance at this pace, it could make blockchain technology obsolete by the end of the decade.
Fortunately, we have time to prepare.
Blockchain systems could be switched to quantum-resistant encryption methods — or Post Quantum Cryptography — before this actually happens. Quantum technologies would replace current encryption algorithms.
The US’s National Security Agency (NSA) has pointed out the need to make this transition, and the US government’s National Institute of Standards and Technology (NIST) is in the process of creating new post-quantum cryptography standards. Expect to see these in the next two years.
These are some potential solutions that different individuals and organizations are working on.
Quantum Resistant Ledger (QRL)
Founded by Peter Waterland, the Quantum Resistant Ledger is the world’s first post-quantum blockchain.
This blockchain eliminates the use of a single private key that can be hacked. Instead, it uses quantum-resistant signatures which change with every transaction. These are secured by Extended Merkle Signature Scheme (XMSS) — a NIST-approved post-quantum digital signature scheme.
Quantum key distribution (QKD)
Developed by researchers at the Russian Quantum Center in 2017, this is an emerging field of cybersecurity.
With QKD, data is encrypted and the key is encoded in qubits. The recipient can measure the qubits to get the key values.
However, following the laws of quantum mechanics, specifically Heisenberg’s Uncertainty Principle, measuring the key causes the state of the qubits to collapse. This means that any intruders would leave a trace simply through the act of measuring the key. This is what makes QKD highly secure.
A quantum networked time machine (!)
In 2018, two theoretical physicists from Victoria University of Wellington — Del Rajan and Matt Visser — proposed a new blockchain design. This quantum blockchain uses particles (photons) that are entangled in space as well as in time.
Here’s how this works: photons are linked chronologically across the blockchain and contain transaction records. While the photons that contained past records can still be read and analyzed, the only photon that exists in the current time is the most recent one.
This means that it would be impossible to tamper with any records because photons containing past records no longer exist. And tampering with the most current photon would collapse the whole system.
Quantum Origin by Quantinuum
Quantum Origin is a quantum key generation platform designed by Cambridge Quantum Computing in partnership with others. This solution can integrate easily with any existing blockchain. It works by introducing a second signature that uses post-quantum keys to secure transactions.
What now?
Adopting quantum-resistant cryptography algorithms and the infrastructure to support them is likely to become a necessity by the latter half of this decade.

But there are a few challenges with this.
Firstly, cryptography is embedded across systems in use today, which makes this a complex task.
Secondly, migrating blockchains is hard, since they are distributed across communities of users — a fork or update could take years to roll out across all users.
Migrating to quantum secure blockchains will also demand increased compute resources since these use large numeric encryption keys and have long processing times.
So what can we do?
Here are a few steps we can take now in order to ensure that we’re ready when the time comes to migrate.
- Inventory all crypto assets, analyze how we’re using cryptography today, and determine which data needs to be secured.
- Cultivate crypto-agility or the ability to respond rapidly to new cryptographic threats. This means being able to adopt new standards without a full overhaul of the existing infrastructure.
- Set up the right governance channels for cryptocurrencies so that communities can be organized and ready to act. Establish a plan of action that covers all points, including any third-party libraries that could be affected.
Mobilizing communities of users to act in unison is no easy task, but it’s one that could spell the difference between success and failure for cryptocurrencies in the future.
Ultimately, it’s unlikely that quantum computing will break cryptosystems. By taking the right steps now, we should be able to keep our data and digital assets safe well into the future.